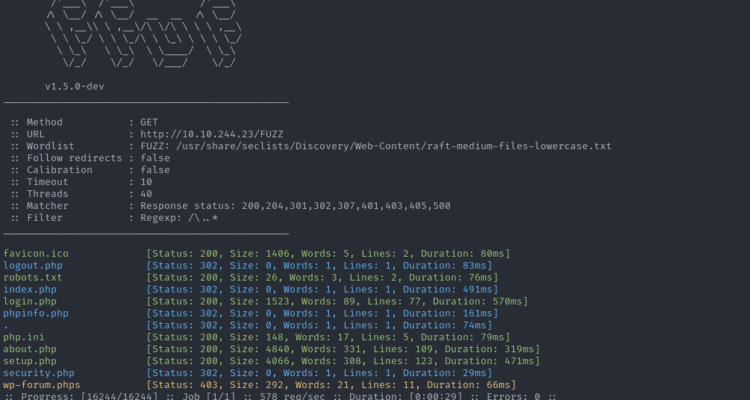
Posted in CyberShare, Exploit, Tools and more
Types of Shells Not just bash shell Intro Once we compromise a system and exploit a vulnerability to execute commands on the compromised hosts remotely, we usually need a method of communicating with