Today we’ll come back to the topic of shells. In...
Read More
Tools and more
Using existing tools doesn’t make you look like a newbie, so don't worry about it, but remember one important thing: always understand how the tool you’re using actually works.
R&E #03: Gathering System Information (Host Enumeration)
Today’s post will be about host enumeration. It is a...
Read MoreExploit #01: Types of Shells – Not just bash shell
Once we compromise a system and exploit a vulnerability to...
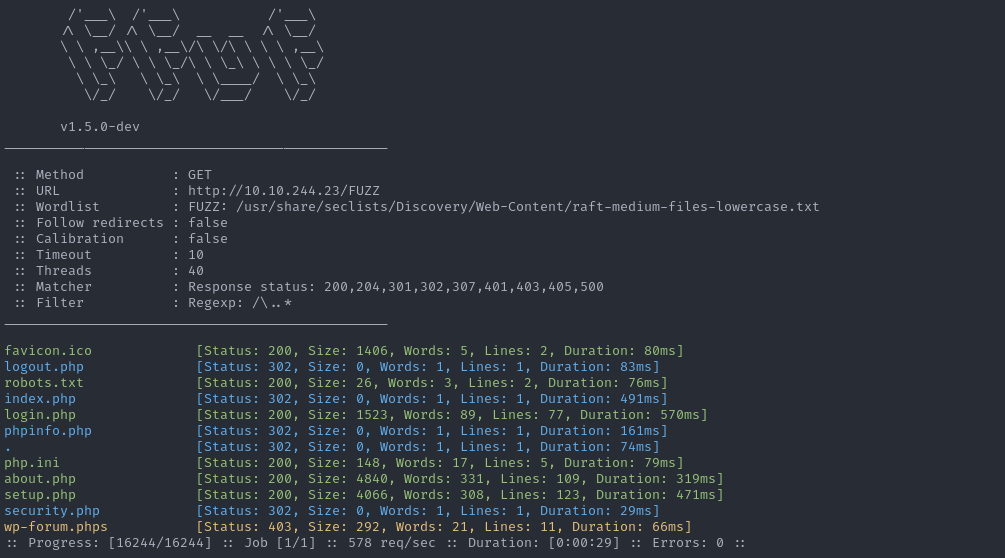
Read MoreR&E #02: ffuf — When you start suspecting that everything hides a path.
ffuf not just a tool, but a pentester’s way of...
Read MoreR&E #01: Nmap – When a attacker inspects your network.
This section will give a brief introduction to Nmap and...
Read MorePost-Exploit: Living Off the Land – Don’t download tools – live with nature.
“LOLT” can be roughly understood as taking advantage of binaries...
Read More