Today’s post will be about host enumeration. It is a...
Read More
Enum & Scan
Gather information about a target network — yeah, you need to do this thoroughly. If you don't, no matter how perfect your payload is, without intel it's just a file sitting on a computer.
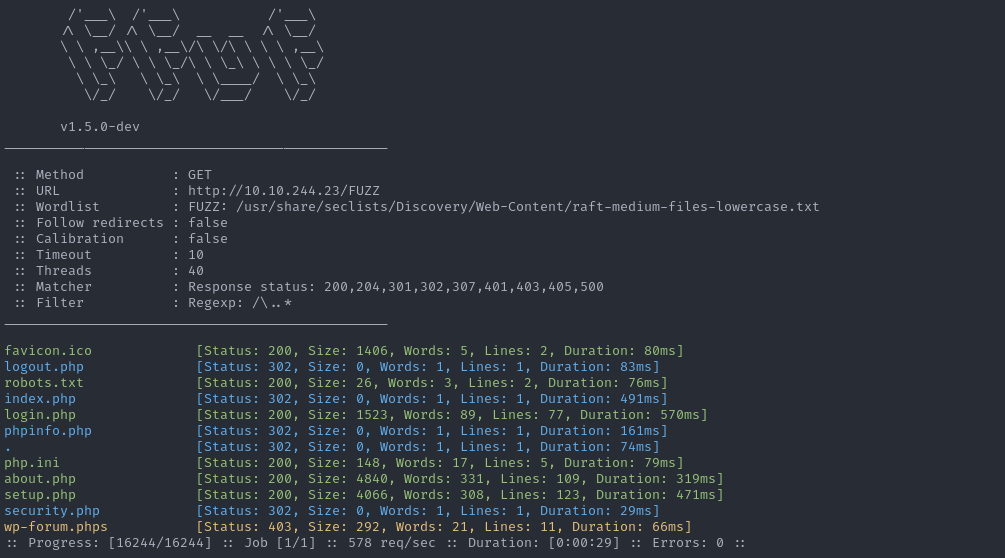
R&E #02: ffuf — When you start suspecting that everything hides a path.
ffuf not just a tool, but a pentester’s way of...
Read MoreR&E #01: Nmap – When a attacker inspects your network.
This section will give a brief introduction to Nmap and...
Read More