Today’s post will be about host enumeration....
Read More
Cyber Sharing
Don’t worry when someone tells you that you’re wasting time reading books or articles on tech-sharing platforms. Everything you read gives you some knowledge — maybe not much, but one day, that small piece of understanding will make a difference.
Linux 101 #03: Linux Workflow (Cont)
A file descriptor (FD) in Unix/Linux operating...
Read MoreLinux 101 #02: Linux Workflow
Let us start with the navigation. Before...
Read MoreLinux 101 #01: Meet Linux: What It Is, Where It Came From, and How It’s Built
Linux, as you might already know, is...
Read MoreExploit #01: Types of Shells – Not just bash shell
Once we compromise a system and exploit...
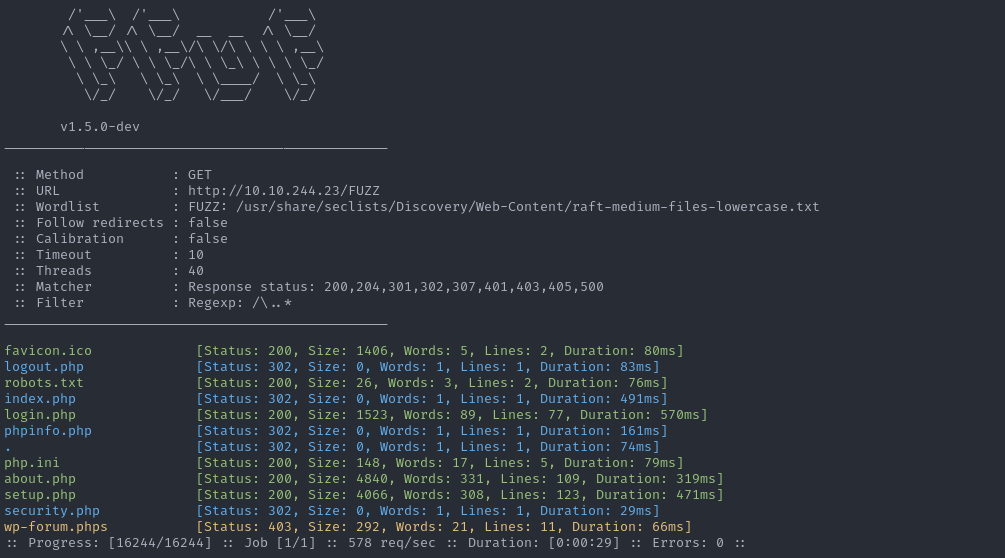
Read MoreR&E #02: ffuf — When you start suspecting that everything hides a path.
ffuf not just a tool, but a...
Read MoreR&E #01: Nmap – When a attacker inspects your network.
This section will give a brief introduction...
Read MorePost-Exploit: Living Off the Land – Don’t download tools – live with nature.
“LOLT” can be roughly understood as taking...
Read More